Biometrics is the science and technology of measuring and analyzing biological data. In information technology, biometrics refers to technologies that measure and analyze human body characteristics, such as DNA, fingerprints, eye retinas and irises, voice patterns, facial patterns and hand measurements, for AUTHENTICATION purposes.
* Increase security - Provide a convenient and low-cost additional tier of security.
* Reduce fraud by employing hard-to-forge technologies and materials. For e.g.Minimise the opportunity for ID fraud, buddy punching.
* Eliminate problems caused by lost IDs or forgotten passwords by using physiological attributes. For e.g. Prevent unauthorised use of lost, stolen or "borrowed" ID cards.
* Reduce password administration costs.
* Replace hard-to-remember passwords which may be shared or observed.
* Integrate a wide range of biometric solutions and technologies, customer applications and databases into a robust and scalable control solution for facility and network access
* Make it possible, automatically, to know WHO did WHAT, WHERE and WHEN!
* Offer significant cost savings or increasing ROI in areas such as Loss Prevention or Time & Attendance.
* Unequivocally link an individual to a transaction or event.
Disadvantages of a biometric system
· The finger print of those people working in Chemical industries are often affected. Therefore these companies should not use the finger print mode of authentication.
· It is found that with age, the voice of a person differs. Also when the person has flu or throat infection the voice changes or if there there are too much noise in the environment this method maynot authenticate correctly. Therefore this method of verification is not workable all the time
· For people affected with diabetes, the eyes get affected resulting in differences.
· Biometrics is an expensive security solution.
WHAT ARE THE POSSIBLE PROBLEM USING BIOMETRICS
One of the most crucial factors in the success of a biometric system is user acceptance of the device. It must cause no discomfort or concern for the user. If people are afraid to use the device, they probably will not use it properly, which may result in users not being granted access.
The biometric device must work correctly. When it functions properly, it does two things: it keeps unauthorized people out and lets authorized people in. No device is perfect. In the biometric world, the probability of letting the wrong person in and right person out, is characterized by the “false accept” and the “false reject” error rates.This contrast and the frustration of dealing with a high number of false rejects will have authorized users and management alike looking for a way to replace the biometric system with something else if these factors are not considered up front.
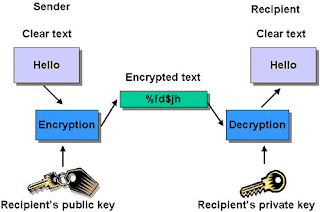
Encryption refers to algorithmic schemes that encode plain text into non-readable form or cyphertext, providing privacy. The receiver of the encrypted text uses a "key" to decrypt the message, returning it to its original plain text form. The key is the trigger mechanism to the algorithm. Today, with online marketing, banking, healthcare and other services, even the average householder is aware of encryption.There are many types of encryption and not all of it is reliable. The same computer power that yeilds strong encryption can be used to break weak encryption schemes. Initially, 64-bitencryption was thought to be quite strong, but today 128-bit encryption is the standard, and this will undoubtedly change again in the future.
ADVANTAGES AND DISVNATAGES OF ENCRYPTION
The single most important reason for using encryption is to preserve confidentiality. This means that only an authorized receiver can read the message (the receiver must have the appropriate decryption key). The disadvantage is the overhead it takes to encrypt and decrypt the messages, especially if a digital certificate is involved, because it may have to
be authenticated as well, and that takes time.
be authenticated as well, and that takes time.

Access control is a system that enables an authority to control access to areas and resources in a given physical facility or computer-based information system. An access control system, within the field of physical security, is generally seen as the second layer in the security of a physical structure. Access control is, in reality, an everyday phenomenon. A lock on a car door is essentially a form of access control. A PIN on an ATM system at a bank is another means of access control.
The possession of access control is of prime importance when persons seek to secure important, confidential, or sensitive information and equipment. Item control or electronic key management is an area within (and possibly integrated with) an access control system which concerns the managing of possession and location of small assets or physical (mechanical) keys. We use our PC day in and day out in almost every feature of our lives. Certainly, working, playing, getting in touch with friends and even shopping can be done right in the comforts of our homes thanks to our PCs and Internet connections. Nevertheless, for something we put your faith in heavily each day, the PC is one of the things we take so easily for granted. Give it some thought - how many of you splurge even just a couple of minutes dusting off your PC?
A firewall is a device or set of devices designed to permit or deny network transmissions based upon a set of rules and is frequently used to protect networks from unauthorized access while permitting legitimate communications to pass.
Many personal computer operating systems include software-based firewalls to protect against threats from the public Internet. Many routersthat pass data between networks contain firewall components and, conversely, many firewalls can perform basic routing functions.
What are the advantages of Firewall Use?
1. A feeling of increased security that your PC and contents are being protected.
2. Relatively inexpensive or free for personal use.
3. New releases are becoming user friendly.
4. You can monitor incoming and outgoing security alerts and the firewall company will record and track down an intrusion attempt depending on the severity.
5. Some firewalls but not all can detect viruses, worms, Trojan horses, or data collectors.
6. All firewalls can be tested for effectiveness by using products that test for leaks or probe for open ports.
Disadvantages of use
- Firewalls evolve due to cracker's ability to circumvent them increases.
- "Always on" connections created by Cable and DSL connections create major problems for firewalls. This can be compared to leaving you car running with the keys in it and the doors unlocked which a thief may interpret as an invitation to "Please steal me".
- Firewalls cannot protect you from internal sabotage within a network or from allowing other user’s access to your PC.
- Firewalls cannot edit indecent material like pornography, violence, drugs and bad language. This would require you to adjust your browser security options or purchase special software to monitor your children's Internet activity.
POSSOBLE PROBLEM: